Overview
The fourth quarter of 2018 saw continued high volumes of banking Trojans, downloaders, and information stealers relative to other malware families. Remote access Trojans (RATs) became increasingly pervasive, email fraud doubled quarter over quarter, and social media support fraud continued its steady growth.
Among the key takeways from Proofpoint’s Q4 Threat Report:
Email remains by far the most common vector for malware attacks and phishing, while the frequency of email fraud continues to rise rapidly. As we observed throughout 2018, the email landscape contained a diverse group of threats, instead of being dominated by any one malware family as occurred in 2016 and 2017. As shown in Figure 1, bankers, downloaders, and information stealers comprised 90% of all malware payloads, but remote access Trojans (RATs) doubled relative to other malware families, appearing in 8% of all campaigns.
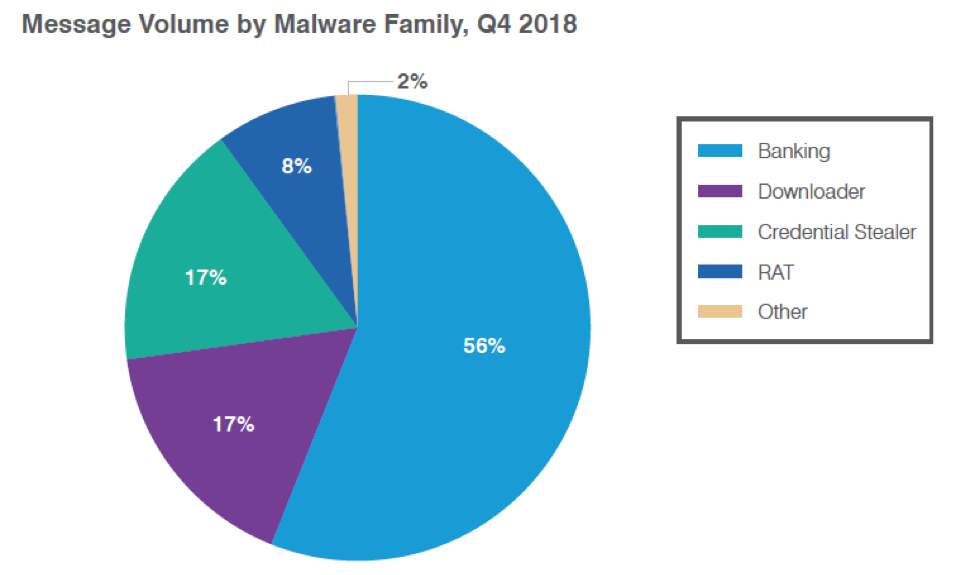
Figure 1: Relative distribution of malicious payloads, Q4 2018
Figure 2 shows the steadily increasing overall message volumes throughout 2018, as well as the relatively steady mix of downloaders, stealers, and bankers across quarters. Note that the minor spike in ransomware in Q2 was basically wiped out in Q4, as ransomware comprised just one tenth of one percent of overall malicious payloads in email.
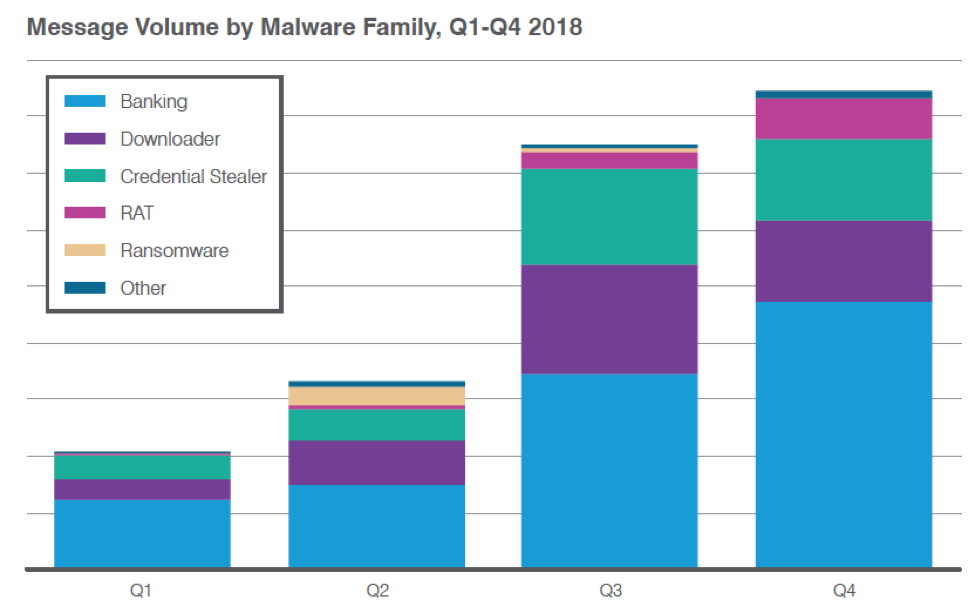
Figure 2: Indexed relative volume of malicious messages by family across quarters for 2018
Email fraud, also known as BEC, continued its rapid growth with the number of attacks per targeted organization increasing 226% vs. Q3 2018 and 476% year over year. Telecommunications, education, and transportation all saw above average growth in email fraud attacks, but no industry was immune and actors targeted companies of all sizes..
Web-based attacks and Coinhive
While exploit kit (EK) traffic remained very low, detected web-based social engineering schemes grew 150% vs. Q3 2018. However, this activity dropped off precipitously at the end of December, a possible seasonal trend that bears further monitoring.
Coinive activity, which has grown continuously over the year, spiked at the end of Q4, with two weeks of activity 23 times the average for the quarter. Again, we will continue to monitor this activity to determine whether this represents a trend or a seasonal anomaly.
Social media
Social media channels remain key vectors for fraud and theft. The platforms themselves have reduced phishing and spam links dramatically but social media support fraud, also known as angler phishing, relies on human interactions. Unlike phishing links, angler phishing increased 442% year over year and 40% over the previous quarter.
Proofpoint Recommendations
The Q4 Threat Report provides insight into the shifting threat landscape that can inform your cybersecurity strategy. Here are our top recommendations for how you can protect your company and brand in the coming months:
Assume users will click. Social engineering is increasingly the most popular way to launch email attacks, and criminals continue to find new ways to exploit the human factor. Leverage a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
Build a robust email fraud defense. Highly targeted, low-volume email fraud attacks often have no payload at all and are thus difficult to detect. Preventing email fraud requires a multilayered solution that includes email authentication and domain discovery, as well as dynamic classification that can analyze the content and context of emails, stopping display-name and lookalike-domain spoofing at the email gateway.
Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile—especially fraudulent accounts that piggyback on your brand. Look for a comprehensive social media security solution that scans all social networks and reports fraudulent activity.
For more information, download the complete Q4 2018 Threat Report.











