Assess: Identify Your Most Vulnerable Users and Top Clickers
 Security Awareness Training
Security Awareness Training
The first step to building an impactful security awareness program is to assess the current state of your program—who your vulnerable users are, what they know, and what they believe. Proofpoint Security Awareness Training provides you with a range of valuable tools, including phishing simulations, tests, culture assessments, and internal cybersecurity assessments. These help you establish a baseline by identifying your most vulnerable users, your Very Attacked People™, what user attitudes and beliefs are about security awareness, and your current gaps. And it allows you to focus your program on real risk by assessing users with real-world threats.
See user risk through a whole new lens
Proofpoint helps you identify your most vulnerable users, including top clickers and users that are being targeted with a significant volume of attacks. With this, you get a data-driven security awareness program that goes beyond phishing simulation. We provide you with unique insights of user risk profiles that are based on users’ interaction with real world threats. This means you can assess and identify those who need the most attention, and easily assign them targeted phishing simulation training with our built-in automation.
Proofpoint also helps you understand how users feel about security and what they believe. Our culture assessment tool provides insights into the current state of your culture so you can determine what needs to be changed.
- Conduct a more targeted, sophisticated phishing campaign that simulates real-world attacks.
- Provide thousands of templates of simulated phishing, SMS, and USB attacks based on lures seen in tens of billions of messages a day by Proofpoint threat intelligence.
- Easily send predefined adaptive learning assessments on today’s most important cybersecurity and compliance topics to get a baseline on user security awareness knowledge.
- Auto enroll users who fall for simulated attacks and fail adaptive learning assessments into targeted simulated phishing tests and additional training.
- Phishing tests allow you to uncover your Very Attacked People and top clickers via integration with the Proofpoint email security solution.
- Assign users short culture assessments to learn more about their attitudes towards security and implement the right changes to motivate users.
Use Threat Intel to Form Your Program
Proofpoint provides your people with timely education of emerging threats seen at scale. Reinforce cybersecurity best practices with threat-driven content and phishing simulations that mimic real-world threats.
Phishing Simulations

You can set up phishing simulations and tests, USB, SMS, and SMShing campaigns in minutes. This allows you to gauge your users’ susceptibility to these important threat vectors. You also get unique insights into user vulnerability. And you can easily see if your users demonstrate consistent positive reporting behavior by flagging simulated messages using the PhishAlarm email reporting button.
Learn More About Very Attacked People
Adaptive Learning Assessments
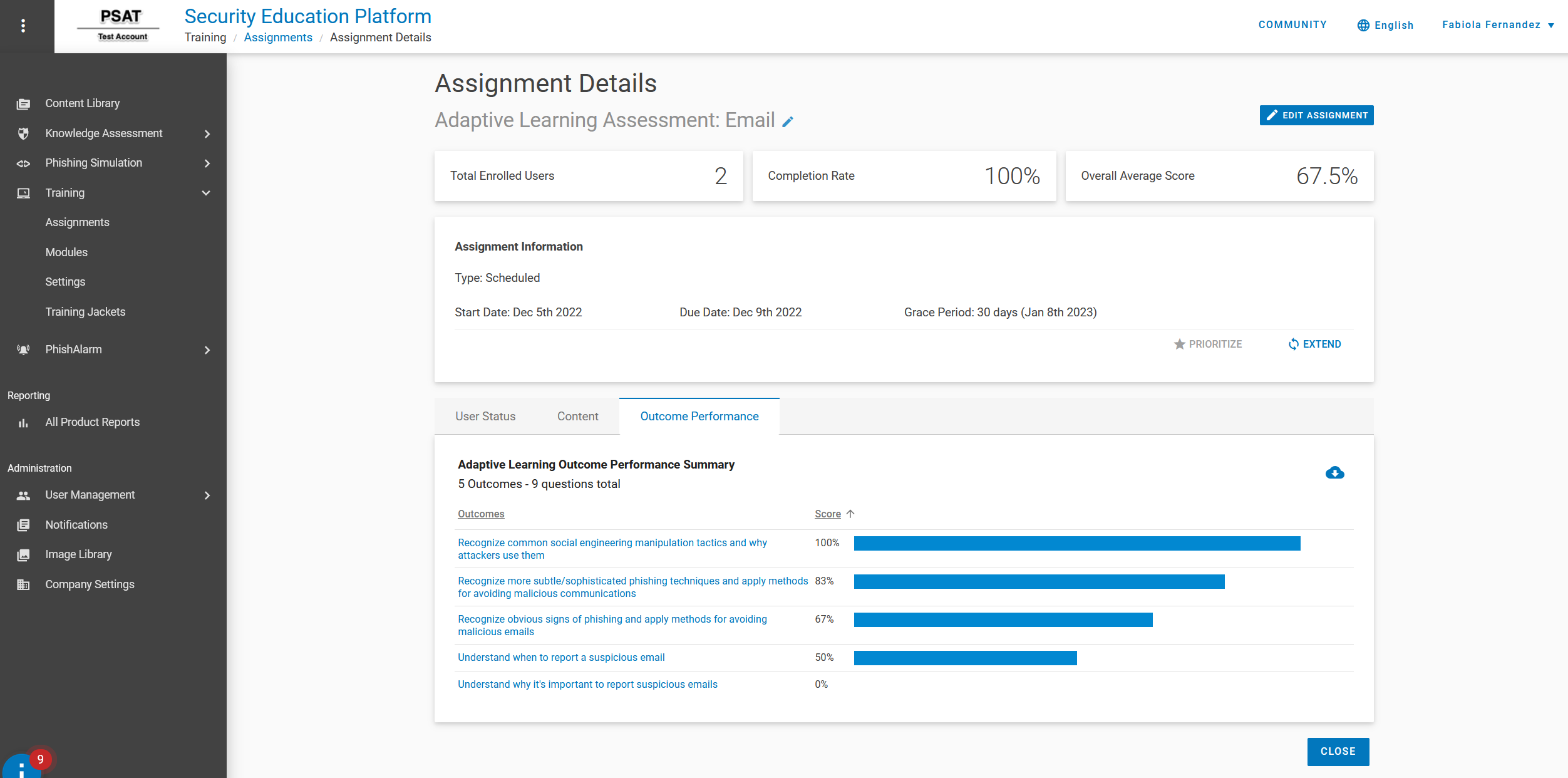
You get predefined cybersecurity assessments and tests on topics such as data protection, passwords, compliance, phishing and more. What’s more, our adaptive learning assessments lets you assign users with questions that relate to the individual training modules you assign—helping you uncover specific user knowledge gaps and decide what training to assign them in the future. Our assessments help you answer questions such as:
- What do my users know?
- Who are my most and least knowledgeable users?
- Which security topics do my users struggle with?
How security-aware are your users?
Culture Assessments
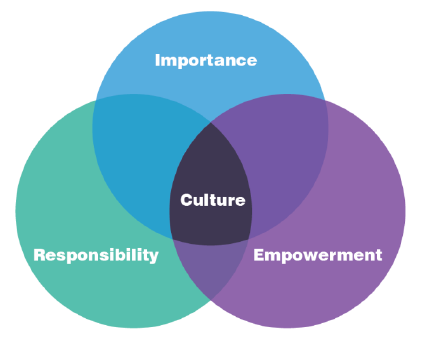
Proofpoint provides a concise survey to help you gauge your security culture, evaluating the three dimensions below:
- Responsibility: Do employees feel that they and their coworkers are responsible for acting to prevent cybersecurity threats?
- Importance: Do employees believe a threat could affect them personally?
- Empowerment: Do employees feel empowered to identify and report suspicious behavior?
Learn more about security culture in this blog.
Learn more about why measuring cybersecurity culture is important and impactful to running an effective security awareness program
Very Attacked People
Dive deeper into the current state of your security awareness program and user vulnerability via integrations with our Threat Protection Platform.

Uncover who your Very Attacked People are. Learn how they’re being attacked and by what types of threats, and whether they’re engaging with malicious messages. By combining this information with simulated phishing test results, you can focus your program on these highly vulnerable users. This will more effectively reduce your overall risk.
Learn more about Very Attacked People and top clickers
People Risk Explorer

Improve your visibility into people risk using vulnerability, attack and privilege data. Using Nexus People Risk Explorer, you can look at a subset of the organization and get a ranked list of risky users. Analyze the list of vulnerabilities based on the security controls you have (such as security awareness training). And get information on the users that each control should be applied to, along with a risk reduction score if a particular control is applied.
Learn more about People Risk Explorer
