Part 2 of 3 in a Series
In this three-part blog series, we explore the practical topics IT and security professionals need to know to fight ransomware. In our previous post, we covered recent ransomware trends that are changing the global ransomware landscape and making it harder for companies to keep pace. In this post, we break down ransomware attacks into eight basic stages to help defenders better understand, conceptualize and communicate how attacks unfold.
Despite a brief drop, ransomware attacks are on the rise again, increasing 62% year over year. They’re costly, too: Research conducted for IBM Security found that the average cost of a ransomware attack is $4.5 million—and that’s not including the ransom. Meanwhile, attackers are focused on creating more sophisticated tools and tactics to skirt companies’ defenses, gain access to accounts and exfiltrate sensitive data.
And although attackers may be constantly finding new ways to get around cybersecurity, it doesn’t mean their tactics are entirely unpredictable. That’s because every ransomware attack typically follows the same basic sequence of events. Here is a closer look at the eight stages of a successful ransomware attack.
Attack chain overview
In most ransomware attacks, bad actors follow these eight steps:
- Reconnaissance
- Initial compromise
- Persistence
- Information gathering
- Privilege escalation
- Lateral movement
- Staging (prior to the attack launch)
- End-stage impact (the result)
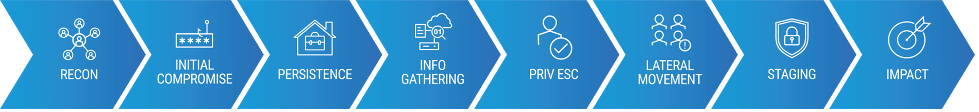
Overview of the eight stages of the ransomware attack chain.
Stage 1: Reconnaissance
This first phase can involve several different types of activity from attackers. Ransomware groups may scan networks looking for machines with unpatched vulnerabilities. Or as in the case of the recent MOVEit zero-day attack, linked to Clop ransomware, a group might be looking to target a specific flaw and research accordingly. And in a small number of cases, ransomware attackers may set their sights on a specific target they believe to be particularly lucrative and research them to identify weaknesses and gather key data about systems and vulnerabilities.
Some of the techniques in this stage include:
- Social engineering. Examples of social engineering tactics include phishing emails, pretexting, phone calls, or in-person interaction. Cyber criminals use these tactics to learn more about their victims.
- Network scanning. Bad actors use network scanning tools to find network systems that are exposed. This includes port, vulnerability and network discovery scanning.
- Open-Source Intelligence (OSINT). Attackers use OSINT tools to learn more about their targets. They collect these details from websites, social media and other public sources.
Stage 2: Initial compromise
For many ransomware operators, the emergence of Initial Access Brokers (IAB) means they can skip ahead to this stage. These large-scale malware operations mostly use a “spray and pray” methodology, sending out millions of malicious messages in the hope that someone will be duped into downloading their malware. At the volumes involved, even a very small success rate can lead to a healthy pipeline of infected machines. IABs then either partner with ransomware operators for a share of the profits or sell access to the highest bidder.
The centrality of IABs to the modern ransomware ecosystem is further proof that people rather than technology are the key vulnerability for most organizations. Verizon reports that 74% of cyber attacks are human activated. It notes that attackers rely on people to execute their code or click a malicious link that leads to an initial compromise.
Attackers will focus on gaining access to the target’s network by using attack vectors and strategies like:
- Malicious URL links and websites
- Credential theft
- Zero-day vulnerabilities
- Recruitment of insiders to grant access
Defenders should keep in mind that attackers will often combine email attacks with these other channels to increase their chances of success.
The threat research team at Proofpoint has recently observed rapid changes in initial access attacks. For example, in 2022, use of Microsoft Office macros for malware delivery decreased by 66%. In the past, IABs relied on macro-enabled documents that were delivered via attachments or URLs to install malware. This technique became all but obsolete last year when Microsoft began blocking macros downloaded from the internet by default.
Right now, we’re seeing a rise in cyber criminals experimenting with different techniques for payload delivery, like HTML smuggling and embedded links in PDFs and other documents. A modern initial access attack might be executed in the following way:
HTML Smuggling → Password Protected Zip → IMG → LNK → QBot
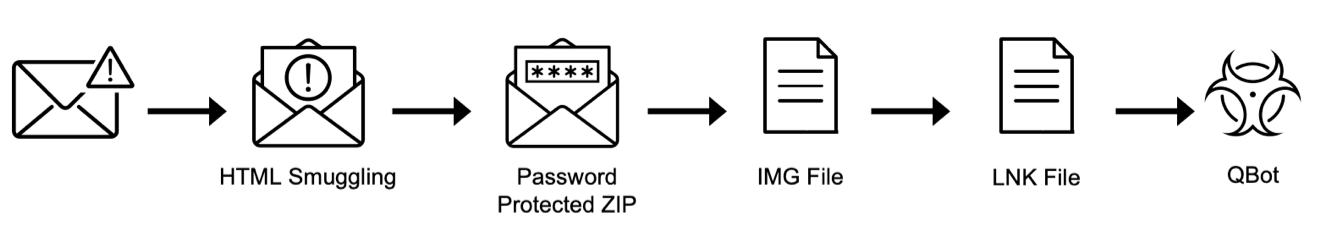
The execution steps of a modern initial access attack.
Moving forward, we expect ransomware actors to continue experimenting with new methods of payload delivery. This will force defenders to move quickly to keep pace. Once attackers have gained access to their target’s network, they begin exploring the system to find other vulnerabilities to establish a foothold. When it comes to stopping them, time is of the essence.
Stage 3: Persistence
After the initial compromise, bad actors will then take steps to maintain access to the target’s network over an extended period. An IAB might do this on their own, or they might sell their access to a ransomware group that will then work to achieve persistence.
In 2022, Coveware reported that 82% of observed ransomware attacks included some form of persistence tactic—up 34% from the previous quarter. Persistence techniques remain relevant because attackers want to protect their hard-won access.
The goal of persistence is to ensure continued access to the target’s network even if the initial compromise is detected and remediated. To achieve this, the attacker might create a virtual backdoor using malware. Or they might modify system configurations to create secret access points. They might also use automated malware persistence mechanisms, such as:
- Exploiting AutoStart locations
- Creating scheduled tasks or services
- Modifying registry entries
- Hijacking legitimate system processes
The malware these bad actors use can be difficult to remediate. It’s often fileless, so it leaves no trace on the victim’s hard drive. It can also become deeply embedded in the operating system, as is the case with rootkits.
Stage 4: Information gathering
At this stage, attackers want to collect critical information about the target’s network and assets. This helps them create high-impact attacks and calculate ransom demands with the highest chance of payment.
The attackers will conduct network reconnaissance and system enumeration to understand the network’s structure, identify vulnerabilities and map potential openings for escalation. They can use this knowledge to target specific systems or services for their ransomware payload. They might use network scanning tools, keystroke loggers and other types of malware in this phase.
Attackers will also begin to identify and exfiltrate valuable data before they encrypt it in the final stage. They perform variations of data discovery to find files and databases that may contain critical information, like intellectual property, financial records or customer data.
Stage 5: Privilege escalation
During this stage, the goal is to secure domain administrator access rights. Attackers accomplish this by using a strategy known as “vertical privilege escalation.” This involves exploiting server misconfigurations and finding system vulnerabilities to gain access to more privileged accounts. Attackers may also use specialist “red team” tools such as Cobalt Strike or Mimikatz.
Poor security access controls, weak passwords, and unresolved misconfigurations make it easy for attackers to succeed at privilege escalation. Not adhering to Zero Trust principles can also leave users with unnecessary access that bad actors can abuse. In our Analyzing Identity Risks Report, Illusive (now Proofpoint) found that 1 in every 6 company endpoints had vulnerable identities that could be exploited for this purpose. Forty percent of those identities, often called shadow admin accounts, could be compromised in a single step.
They might also focus on breaching systems such as Active Directory (AD) or Microsoft Azure, which serve as central repositories for user accounts, permissions and authentication data. By accessing AD, attackers can gain insight into the network’s structure and user privileges. These techniques can be highly effective, and their insights can help them to compromise administrative accounts.
Stage 6: Lateral movement
As the name suggests, lateral movement refers to threat actors moving across the network to expand their reach.
To achieve higher payouts, ransomware actors will encrypt entire systems and exfiltrate sensitive data from various internal sources. They need as much access as possible to accomplish their goals. Lateral movement is especially widespread in ransomware attacks. However, it’s not exclusive to these types of attacks. Research that VMware conducted for its 2022 Global Incident Response Threat Report found that lateral movement was used in up to 25% of all incidents.
As ransomware actors traverse through a company’s systems, they repeat the process of escalating privileges on other devices and compromising additional hosts. They use many tactics already discussed, including exploiting unpatched software and stealing credentials. They might also leverage remote desktop protocols (RDP) and other legitimate services such as Windows Management Instrumentation (WMI), Server Message Block (SMB) or PowerShell.
Lateral movement helps attackers locate critical assets. It also helps ensure widespread encryption of data during the impact phase. This strategy played a critical role in last year’s Uber breach, and in the high-profile SolarWinds attack in 2020. In short, lateral movement is a crucial step in the attack chain that defenders must be prepared to address.
Stage 7: Staging
The attackers are now ready to prepare and position their ransomware within the victim’s environment. The staging phase occurs after the attackers have gained initial access to the victim’s network but before they encrypt any data. It is the last crucial step before impact. (It’s also the last chance for defenders to prevent the final attack.)
Ransomware actors will carefully plan and execute actions to optimize the impact of their attack and minimize the chances of recovery. Steps they may take during staging include:
- Customizing their ransomware code to suit specific attack objectives
- Testing their delivery mechanisms
- Confirming communication channels with their command-and-control infrastructure
The staging phase is also their final chance to exfiltrate data to use in double- and triple-extortion techniques. Ransomware actors often demand several payments. The first is for decrypting files or systems. Subsequent demands might be for payments for returning or destroying exfiltrated data. Sophos reports that more than 30% of ransomware attacks in 2022 involved data extortion.
Final stage: Impact
The impact phase is the point where attackers will execute their final attack, notify the victims of their security breach, and encrypt the victim’s network or data. The “impact” may include rendering business-critical systems inaccessible until a ransom is paid.
For many businesses, the impact is the first indication of a ransomware attack.
The steps in this phase can vary, depending on the end goal of the attacker. However, it usually includes:
- Encryption. Once the ransomware is triggered, it spreads across the network rapidly, encrypting files and locking users out of their systems. The time it takes to full encryption depends on many system variables. But overall, this process is getting faster—emphasizing the need for detection earlier in the attack chain.
- File renaming or extension changes. Ransomware may rename or change file extensions to indicate that the files have been compromised and require decryption.
- Ransom note display. Attackers need to establish communication with the victim and provide instructions on how to pay the ransom and obtain the decryption key.
In some cases, ransomware may take additional steps to lock users out of their devices or networks to disrupt the victim’s systems further. Or they might skip encryption to focus on extortion tactics.
Breaking the attack chain
Ransomware attacks keep evolving. To combat this persistent threat, companies must stay informed, adapt their defenses and foster a culture of cybersecurity awareness. Each stage of the ransomware attack chain presents opportunities for proactive defense and mitigation.
In the final part of this blog series, we’ll look at ransomware prevention strategies and security controls to address each step in the cyber kill chain.
Take a rapid risk assessment
Meanwhile, if you’re concerned about the risk of ransomware to your business, consider taking the Proofpoint Email Rapid Risk Assessment. This free assessment takes only five minutes, but it has a big impact.
It can not only help you to uncover threats that your current security solution might be missing, but it can also help you understand which users in your company are being targeted by attackers. These insights can help you understand why the best defense against ransomware threats is integrated and layered protection.











