Conversational threats on the rise as smishing growth slows. And a look back at 2023 on our weekly podcast.
This week on The Threat Hub: As we enter the final stretch of the holiday shopping season, “missed delivery” SMS phishing—or smishing—messages remain a regular nuisance. But there’s some good news. A new blog post reveals that over the past 18 months, smishing growth has slowed in many regions, becoming part of the landscape rather than a rising threat. However, while these malicious messages are now familiar to most, conversational threats are still on the rise, increasing over 300% in the past year.
Pig butchering has grabbed a lot of headlines recently—including this week in the New York Times—but it isn’t the only type of conversational attack. Impersonation attacks have become commonplace in some parts of the world. In the U.K., a favored tactic is pretending to be a family member with a lost or broken phone. A classic example of social engineering, this lure uses parental anxiety to bypass caution and increase the chance of engagement. Similar attacks have been reported in New Zealand, and the U.S. may not be far behind.
And on this week’s Five-Minute Forecast, authorities issue warning about Play ransomware attacks on infrastructure, Qbot returns only months after law enforcement action, and senior threat research manager Daniel Blackford shares reflections on the 2023 threat landscape.
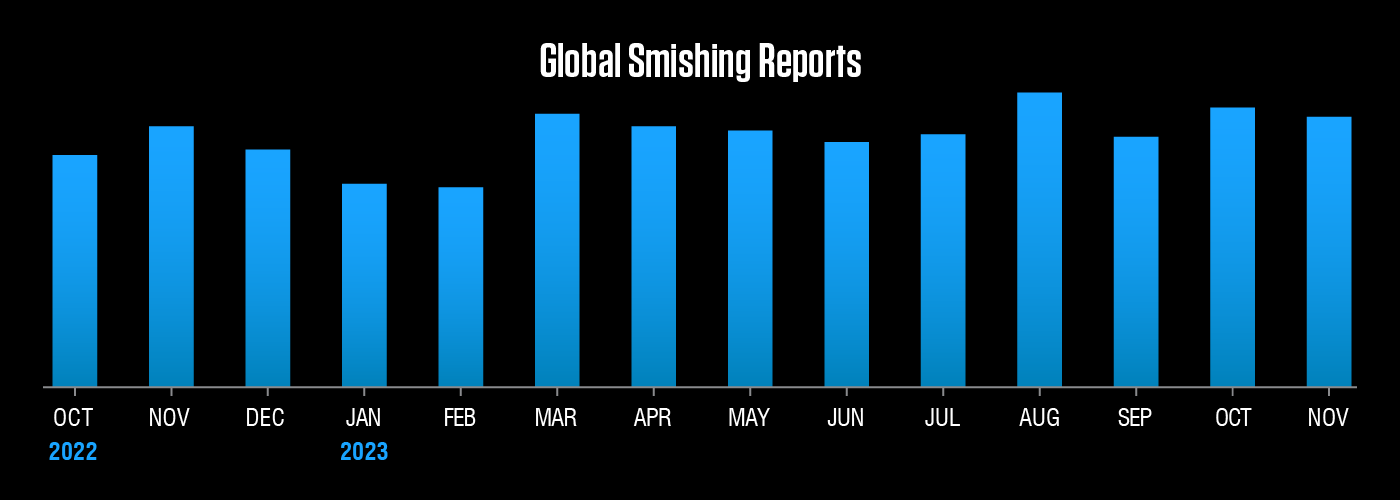
After experiencing extraordinary growth over the past few years, smishing has now become an established part of the threat landscape. But while the rate of increase may have slowed, absolute volumes of malicious SMS—and risk to consumers and businesses—remain high.
Equip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.


