Cybersecurity stop of the month takes aim at MFA manipulation. And reviewing early moves on the 2024 threat landscape.
This week on The Threat Hub: As more businesses adopt cloud-based platforms, cybercriminals are finding new ways to compromise them. And one of the most powerful techniques at their disposal is multifactor authentication (MFA) manipulation. This is a post-delivery attack that allows bad actors to bypass or insert their own MFA methods into cloud accounts. A recent blog post explains how this attack works and why it poses a significant threat to cloud security.
MFA manipulation can take different forms, such as adversary-in-the-middle (AitM) attacks, where the attacker intercepts the user’s credentials and session cookie. Proofpoint recently detected and prevented a series of MFA manipulation attacks on a large real estate company, where the attackers used the “My Sign-Ins” app to add their own MFA methods to compromised Microsoft 365 accounts. This enabled them to authorize malicious third-party applications and maintain persistence even after their initial access was cut off. The blog post also offers some best practices to protect your cloud accounts from MFA manipulation, such as conducting regular audits, educating users, and using automated tools to monitor and remediate threats.
And on this week’s Five-Minute Forecast, CISA issues a high-severity alert over SharePoint vulnerability, fake 401(k) statements are being used as lures in credential phishing spree, and a January threat landscape overview from Selena Larson.
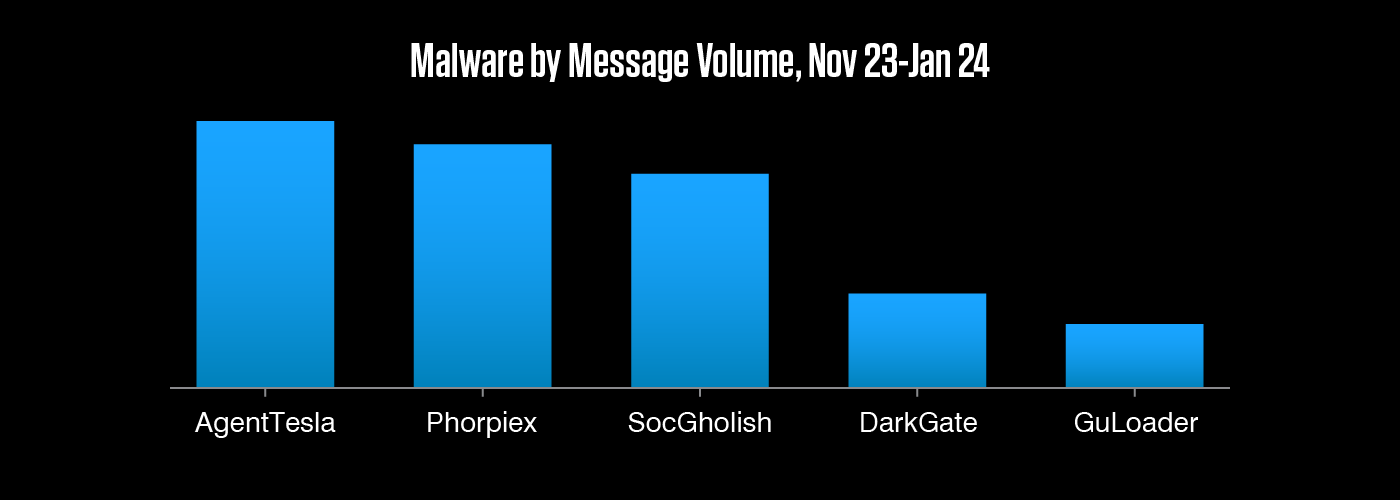
It won't surprise to many to find threat landscape stalwarts AgentTesla and SocGholish among the top malware over the holiday period. But a high-volume DarkGate campaign in November and a very large Phorpiex campaign in December were enough to propel these newcomers into the top five.
Equip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.


