The Discarded Podcast team shares predictions for 2024. And our researchers open a file on DarkGate malware.
This week on The Threat Hub: We start the new year with a special episode of the Discarded podcast. Hosts Selena and Crista are joined by senior threat managers Daniel Blackford and Alexis Dorais-Joncas for a look back at the 2023 threat landscape, and a look forward at what defenders will be dealing with over the coming months. Predictions cover developments in the use of traffic-distribution systems, modular attack chains and adoption of non-corporate infrastructure to evade detection. The team also looks at potential activity spikes ahead of this summer’s Olympic Games in Paris.
In the last weeks of December, our researchers published a blog post looking at trends related to DarkGate, a relatively new malware strain that rose to prominence during the summer and fall. Multiple cybercrime actors have used DarkGate, but a distinct cluster of activity caught the attention of our team. The cluster isn’t currently attributed to a known threat actor, so it has been dubbed “BattleRoyale” for now. We’re continuing to monitor BattleRoyale, which is notable for using both email and fake browser updates to deliver its payloads. Check out the full blog post for more details of our investigation, as well as a list of Emerging Threats signatures and IoCs.
And on this week’s Five-Minute Forecast, LockBit ransomware threatens to release sensitive medical data, crypto-draining scams soar on social media, and Selena Larson explains the significance of DarkGate and BattleRoyale.
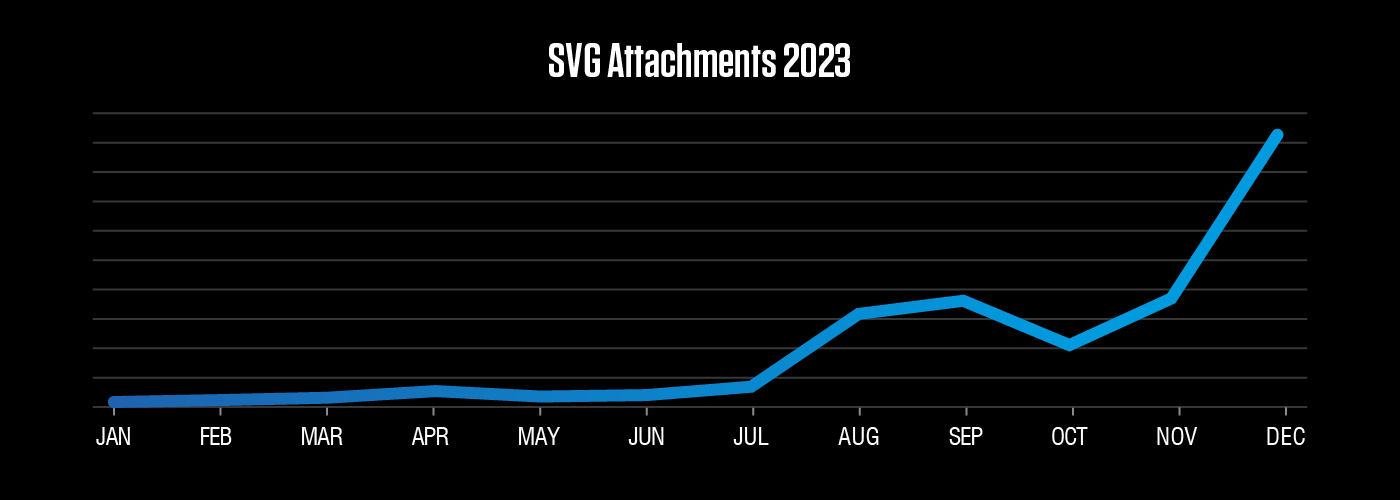
Scalable vector graphics (SVG) files are typically used for web graphics and support animation and interactivity. But they can also be used to maliciously smuggle various filetypes or scripts. Our researchers have seen SVG files used in the past, but their prevalence in our data increased dramatically towards the end of the year.
Equip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.


