A prominent crimeware threat actor returns after a lengthy absence. And all the latest cybersecurity news on our weekly podcast.
This week on The Threat Hub: After a nine-month absence, TA866, a notorious e-crime threat actor, has returned with a large email campaign targeting North America. The attack chain involves several steps, starting with an invoice-themed email containing a PDF attachment with a OneDrive link. If clicked, the link initiates an infection sequence that ultimately leads to a custom malware payload of the WasabiSeed and Screenshotter toolset.
Despite the large gap between campaigns, this activity is attributed to TA866 based on similarities with previous observations from March 2023, as well as the group’s ownership of the malware payload. The post also highlights the involvement of another threat actor, TA571. In this campaign, TA571 distributed the initial email and PDF attachment, with TA866 taking over post-exploit. Check out the security brief on our blog for more details, including a list of IoCs and Emerging Threats signatures.
And on this week’s Five-Minute Forecast, Microsoft is hit by attack from Russian state-sponsored hackers, 3AM ransomware is linked to the defunct Conti group, and Selena Larson shares some details on the return of threat actor TA866.
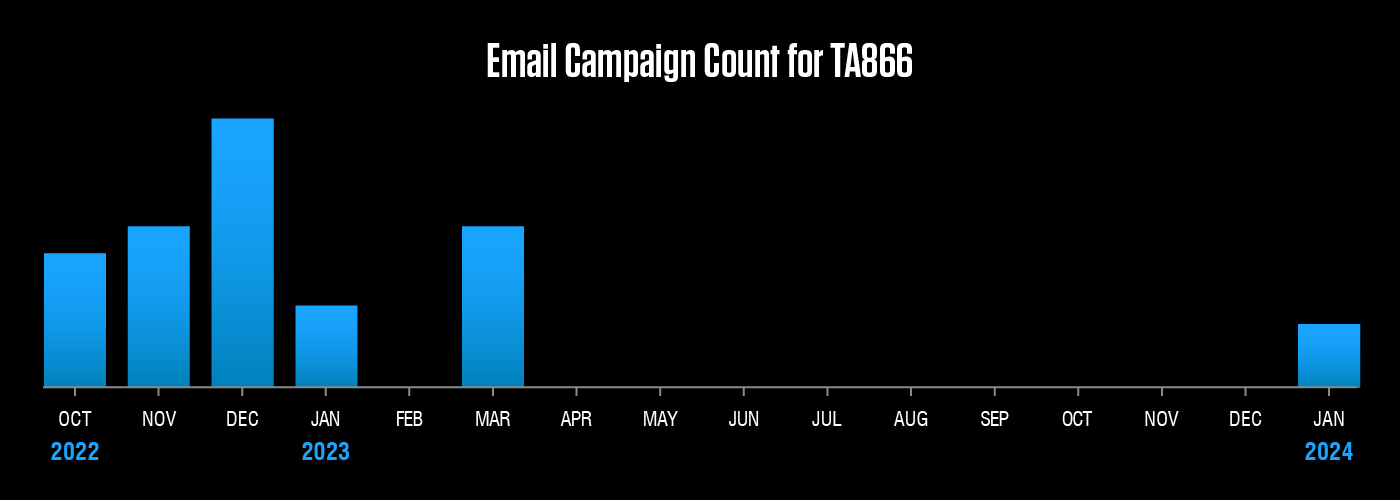
After a nine-month hiatus, e-crime threat actor TA866 returned in January with a new campaign and a new attack chain. But some things remain the same, with the group still favoring their custom WasabiSeed and Screenshotter toolkit.
Equip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.


