Mobile devices court risk on many levels, from malware to network compromise to outright theft. While many of these risks can be mitigated with technical solutions, one threat is extremely difficult (if not impossible) to control: the users themselves.
The near ubiquity of smartphones and tablets multiplies the risk of data breaches and successful cyberattacks. According to the 2017 AT&T Global State of Cybersecurity survey, 51% of organizations said employee mobile devices were the source of a breach — yet only 61% require employees to participate in security awareness training. BYOD environments are particularly challenging, since employee-owned mobile devices typically contain a mix of enterprise tools and personal apps, and the sheer number and variety of devices makes policing user behaviors extremely difficult.
Users put your organization’s data at risk every time they download a vulnerable or malicious app, and also when they fail to update apps and their device’s OS. Even when users show reasonable caution, they may be inadvertently giving away sensitive information.
Security Risk Example: Ritual
A recent example of mobile apps leaking sensitive information is the “social” food-ordering app, Ritual. Part of Ritual’s appeal is that it connects users within the same workplace, allowing them to “piggyback” on each other’s orders; five people might place separate takeout orders, but one person can pick them up.
The problem, as reported in March by Engadget, is that Ritual shares users’ precise workplace information, such as building address and floor, as well as when and where users are picking up a meal. In addition, anyone can “join” any company on Ritual without any verification that they actually work there. Total strangers can sign up for Ritual and learn employees’ office locations at organizations like the US Department of Homeland Security (DHS), Lockheed Martin, the Pentagon, and more. This access could prove invaluable for social engineers and other criminals who want inside information about a particular organization.
As Engadget noted, “While the idea behind Ritual makes sense, it’s shocking that there aren’t better privacy controls and data sharing options … there’s rampant potential here for abuse.”
This single instance illustrates a two-fold problem for infosec professionals:
- How can you identify the hidden dangers of every seemingly innocuous app available in mainstream app stores?
- How do you prevent users from downloading and using potentially harmful apps?
Mobile App Security Risks
The DHS’s 2017 Study on Mobile Device Security examines vulnerabilities and risks throughout the mobile ecosystem, and pays considerable attention to apps. As represented in the study’s “Threats via Mobile Apps” illustration (see below), there are multiple ways that malicious apps can exploit mobile devices.
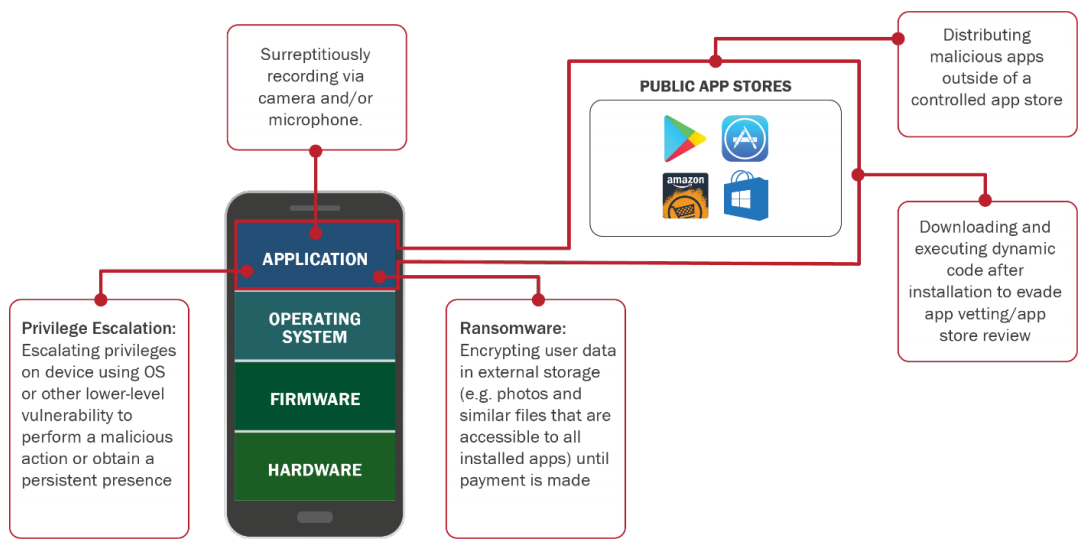
Source: Department of Homeland Security, Study on Mobile Device Security, 2017.
Malicious mobile apps are “intentionally designed to gather or compromise sensitive data,” the DHS study cautions. “In many cases, this is done without the user’s knowledge or acceptance, but in some cases the app requests access to data or services when installed that exceeds the permissions necessary for full functionality without the user’s understanding of the consequence.” While more savvy users might see a red flag when a new app requests needless access to their contacts or camera, many average users would grant permission without much of a thought.
Risks with malicious apps include the following:
- Gathering privacy-sensitive information
- Surreptitious eavesdropping
- Exploiting access to sensitive enterprise networks or data
- Ransomware infections
- Enabling other types of fraud or malicious practices
- Attempting to root/jailbreak a mobile device
- Manipulation of trusted apps
- Sharing of data between trusted apps
But even non-malicious apps introduce risk through a range of vulnerabilities:
- Insecure network connections
- Files stored with insecure file permissions or in an unprotected location
- Sensitive information written to a system log
- Web browser vulnerabilities
- Vulnerabilities in third-party libraries
- Cryptographic vulnerabilities
How Careless App Users Become Unintentional Insider Threats
The average mobile device user has grown accustomed to the near-instant gratification offered by app stores, and may not know (or care) about security best practices, such as vetting apps and updating their device’s OS. An article by IT firm Forsythe notes that these users can become unintentional insider threats by operating mobile devices that leak sensitive data for any cybercriminal to gather.
“Most people download applications from app stores and use mobile applications that can access enterprise assets without any idea of who developed the application, how good it is, or whether there is a threat vector through the application right back to the corporate network,” the Forsythe authors noted. And they caution that a related issue arises when employees use personal cloud services on mobile devices as a kind of shadow IT: “when used to convey enterprise data, these applications can lead to data leaks that the organization remains entirely unaware of.”
The Need for Vigilance and Cyber Hygiene
A variety of tools allow infosec teams to remotely manage mobile devices — including employees’ personal smartphones — and control device configuration, enterprise content generation, and more. But even with these technologies in place, organizations are still at the mercy of end users, to some degree. Will they download vulnerable or malicious apps, installing malware on their devices? Will they download apps from risky third-party stores onto jailbroken devices (known as sideloading)?
The issue is somewhat analogous to phishing. While plenty of tools exist to prevent phishing attacks from reaching users’ inboxes, some will slip through. And when that happens, an organization’s best defense is to have vigilant end users who are well-versed in cybersecurity best practices. Similarly, when users are browsing mainstream app stores, those who have participated in security awareness and training will be much more likely to identify and avoid potentially vulnerable and malicious apps.
Combining Technical Tools with Security Awareness and Training
The DHS’s Study on Mobile Device Security details many technical strategies for defending against vulnerable and harmful mobile apps, but it places particular emphasis on end-user security awareness and training. “Similar to the situation with threats to PCs, user awareness and training is the first and often the best defense against many threats. Understanding the threat landscape and maintaining up-to-date software can be a significant deterrent,” the study states. “Additionally, users should avoid (and enterprises should prohibit on their devices) sideloading of apps and the use of unauthorized app stores.”
When it comes to BYOD and corporate device management, the best solution for organizations is the same as with other sources of end-user risk: a combination of technical tools and a commitment to cybersecurity education. In addition to applying mobile management tools, infosec teams should provide employee awareness and training that emphasizes mobile device security and mobile app security. The two approaches complement one another, offering protection against insider threats as well as external attackers.


