Overview
Proofpoint researchers have been following a previously undocumented threat in which actors are stealing bitcoins via the Tor proxy onion[.]top. Operators of this proxy are surreptitiously diverting Bitcoin payments from ransomware victims to their own wallets by modifying in transit the source of web pages used for payment, replacing the ransomware author-controlled Bitcoin addresses with their own. As a result, the proxy operators are not only preventing ransomware victims from decrypting their files by paying a ransom but are also in effect stealing from the threat actors distributing ransomware. This appears to be the first scheme of this type affecting both ransomware victims and operators.
Background: Tor Proxies
Many strains of ransomware present victims with a payment demand, where victims must visit a Tor .onion site to complete the payment to a specified Bitcoin address. As most users typically do not have a Tor browser installed, they may use a Tor Proxy instead – some ransom notes even suggest that they do so. Tor proxies are regular websites that translate Tor traffic into normal web traffic. However, this gives the Tor proxy operators unlimited power to replace content, acting as a man-in-the-middle.
Tor proxies are simple to use. Users typically add an extension such as .to, .cab to in the onion URL, and it becomes usable in a normal browser. For example, in order to use hxxps://robusttldkxiuqc6[.]onion/, users need a dedicated Tor browser. However, they can use hxxps://robusttldkxiuqc6[.]onion[.]to/ in any browser.
There are several providers of the proxy services with onion[.]top among the most popular. To use their service, users add the .top extension after the .onion domain.
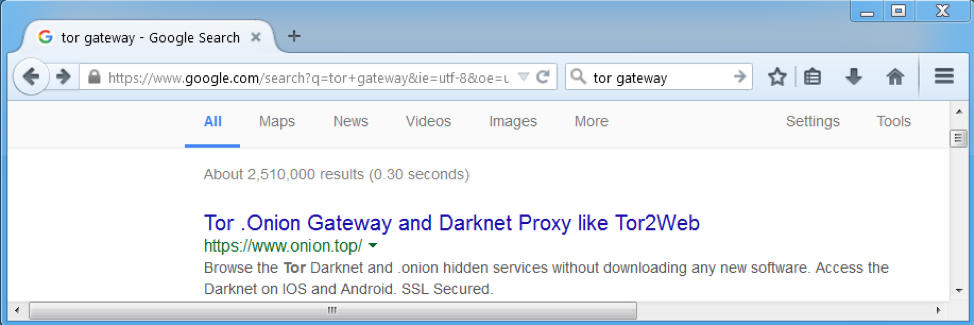
Figure 1: A search for “Tor gateway” or “Tor Proxy” typically returns onion[.]top’ service as one of the first results (personalized search results were turned off for this example)
LockerR
We first learned of this behavior through a message on the LockeR ransomware payment portal urging victims not to use onion.top to pay their ransoms (Figure 2).
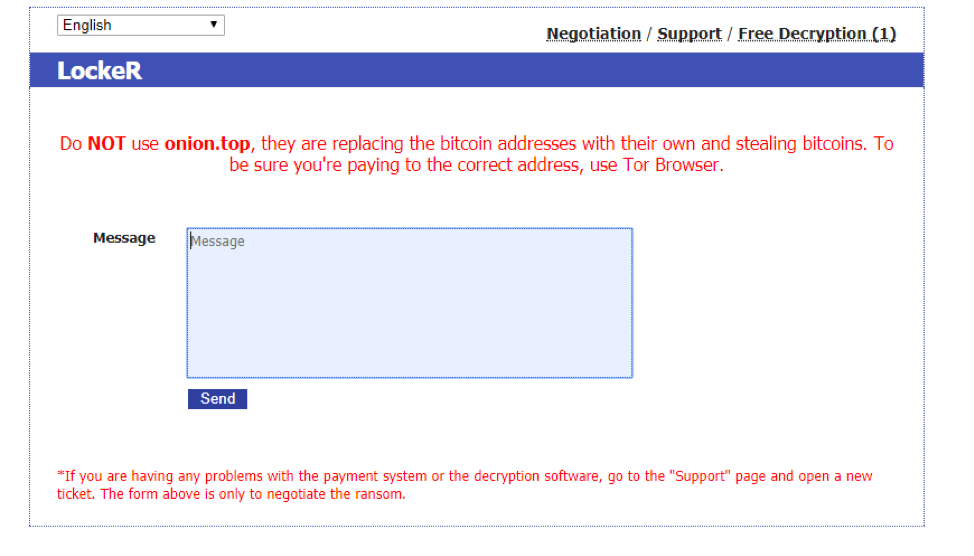
Figure 2: LockeR ransomware payment portal requesting that victims not use onion.top
Other researchers have documented similar behavior with the Evrial information stealing Trojan that monitors the Windows clipboard for Bitcoin payment addresses (among other strings such as like those related to Steam payments) and replaces those addresses in the clipboard with addresses under attacker control.
LockeR was first observed in October 2017 [1]. Most recently, it was delivered via an instance of the RIG-v exploit kit in a malvertising campaign. We compared the same LockerR payment site viewed in both the Tor browser and via the .top Tor proxy. As expected, the Bitcoin address was replaced in the page accessed via onion.top (Figure 3).
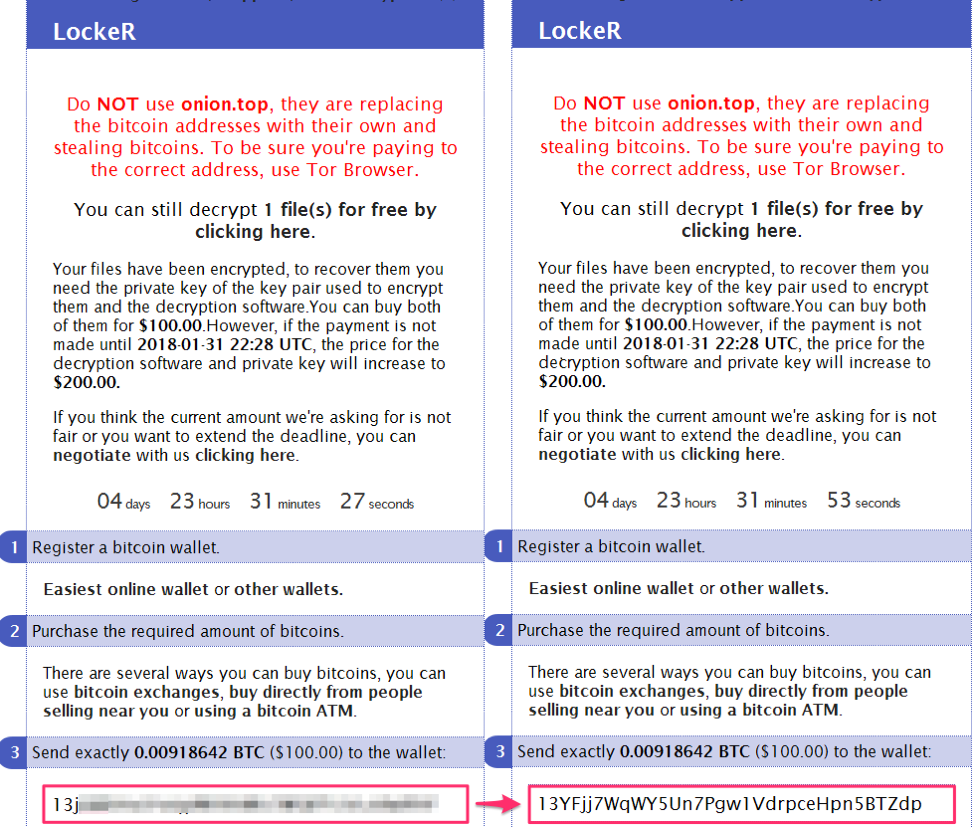
Figure 3: LockeR payment domain as viewed with the Tor Browser (left) and via the .top Tor proxy (right)
In the left pane of Figure 3, the LockeR payment domain displayed with Tor Browser shows the correct Bitcoin payment address. For LockeR ransomware, these payment addresses are unique to each victim. On the right, the same payment domain viewed with .top Tor proxy displays a different Bitcoin address. While we do not know the exact algorithm for selection of substitute addresses, it appears that onion.top substitutes same Bitcoin address for all LockeR victims.
GlobeImposter
We then tested another currently popular ransomware, GlobeImposter [2].
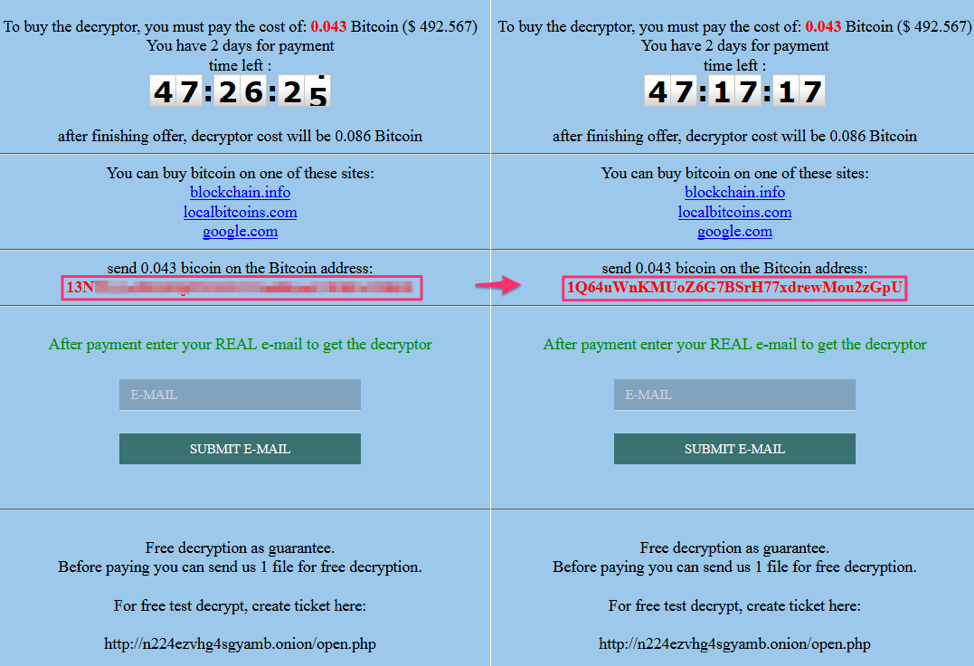
Figure 4: GlobeImposter payment domain as viewed with the Tor Browser (left) and via the .top Tor proxy (right)
Again, as shown in the left pane of Figure 4, the GlobeImposter payment domain viewed with the Tor Browser shows the correct Bitcoin payment address. As with LockeR, payment addresses are unique to each victim. On the right, the same payment domain viewed with the .top Tor proxy displays a different Bitcoin address. Note that this address is different from the substituted address used for LockerR.
In one case, due to an apparently buggy substitution routine, the replacement address was displayed with an extra three characters at the end -- the final three from the original address -- and was therefore invalid.
Sigma Ransomware
Finally, we performed the same test with Sigma ransomware.
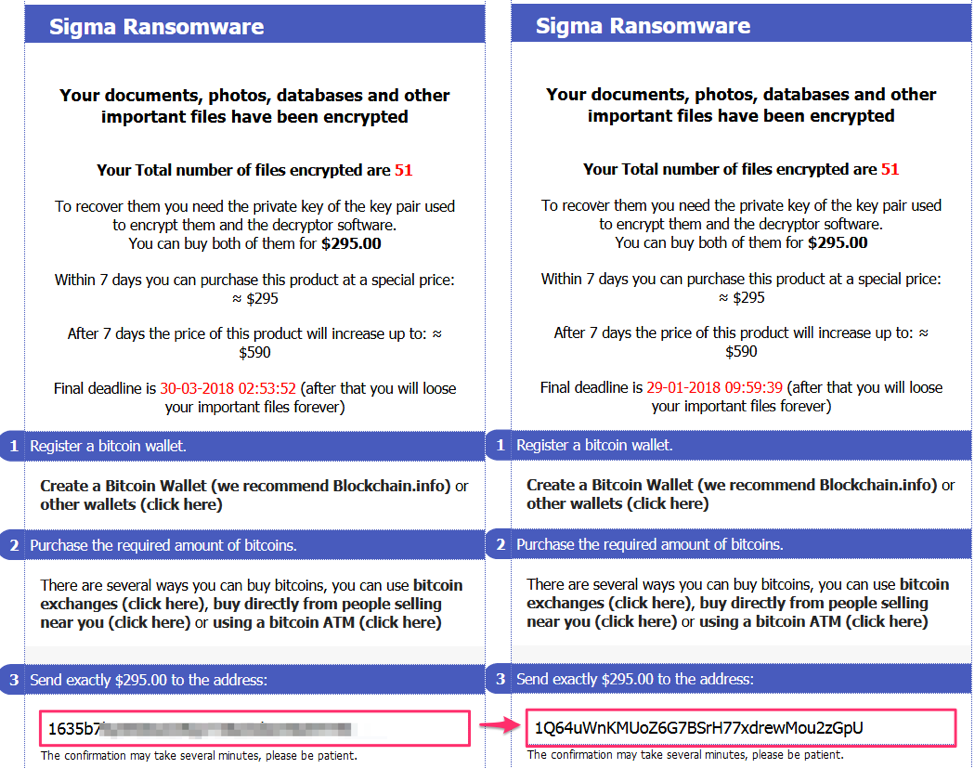
Figure 5: Sigma ransomware payment domain as viewed with the Tor Browser (left) and via the .top Tor proxy (right)
Similarly, we observed the Bitcoin address replaced for Sigma ransomware victims attempting to make payments via the .top Tor proxy. Note that the replacement address was the same as that for GlobeImposter (1Q64uWnKMUoZ6G7BSrH77xdrewMou2zGpU).
Diverted Bitcoin Amounts
We examined at the replacement Bitcoin addresses to determine how much may have been stolen by the proxy operators. The Bitcoin address 13YFjj7WqWY5Un7Pgw1VdrpceHpn5BTZdp has had a total of 0.15 BTC transferred to it ($1,661 at the time of publication - see Figure 6). The Bitcoin address 1Q64uWnKMUoZ6G7BSrH77xdrewMou2zGpU has had a total of 1.82 BTC transferred to it ($20,154 at the time of publication - see Figure 7). We do not know if other Bitcoin addresses are being used in this scheme.
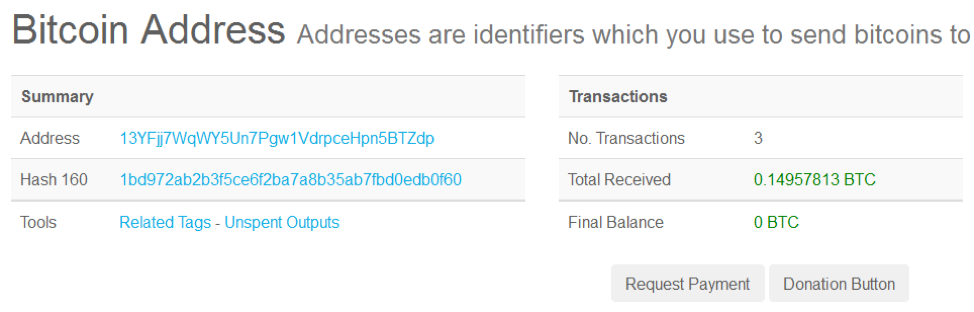
Figure 6: Amounts transferred to 13YFjj7WqWY5Un7Pgw1VdrpceHpn5BTZdp address
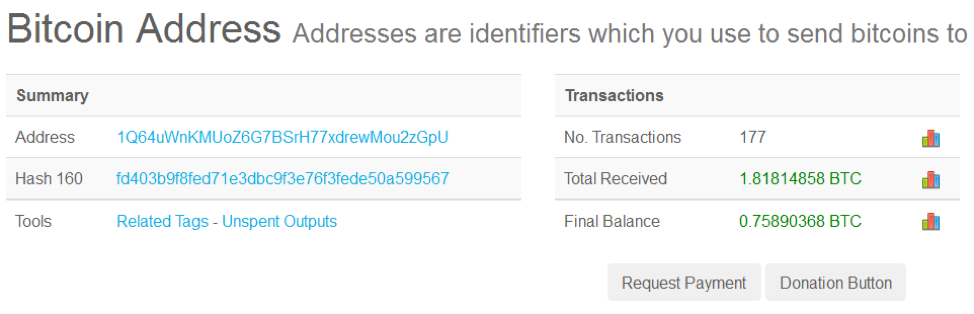
Figure 7: Amounts transferred to 1Q64uWnKMUoZ6G7BSrH77xdrewMou2zGpU address
Final Notes
It does not appear that the .onion.top attempt to redirect payments for all ransomware variants. For example, the BitPaymer ransomware Bitcoin address was unchanged in our tests.
Sophisticated ransomware operators appear to be aware of this behavior and are attempting to mitigate with “user education” and technical workarounds.
For example, when LockeR was first observed, the operator, like many others, was apparently not aware of the scheme and even included the .onion.top links in their ransom note (see pictures in [1]). They have since removed the .top links from their note and added a warning in red text to their ransom notes for victims.
Magniber ransomware [3] appears to combat Bitcoin address replacement by splitting it into four parts in the HTML source code, making it harder for proxies to detect the Bitcoin address pattern:
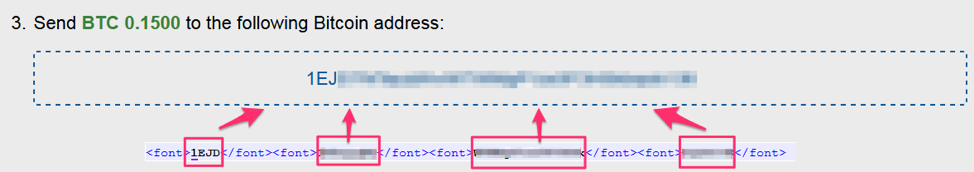
Figure 8: Magniber technique to combat Bitcoin address substitution
GlobeImposter ransomware urges users to use the Tor browser and hides the .onion payment address from the victims. Instead of providing it as a link in ransom note, it is obfuscated in the note, and deobfuscated at run-time when the user clicks a button.
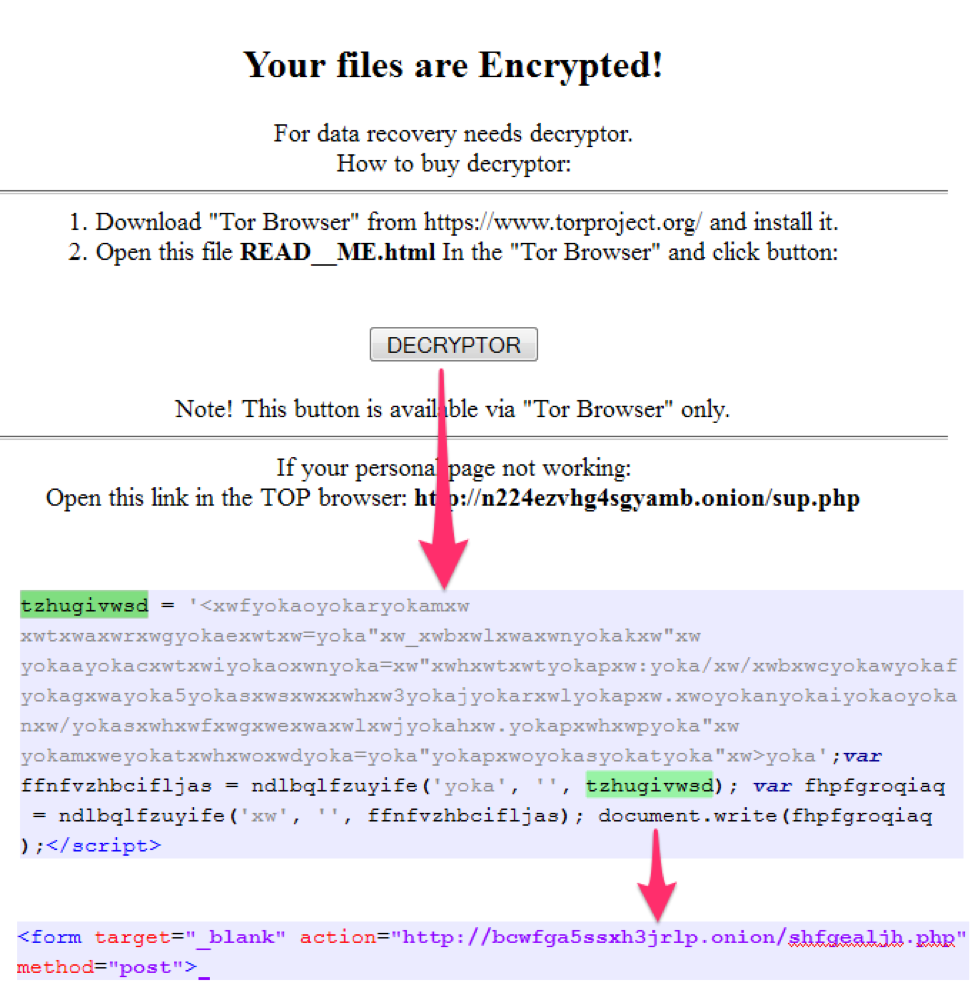
Figure 9: GlobeImposter technique to dissuade proxy use for the "personal" payment address
Conclusion
While it appears that operators of onion.top have not stolen a large number of bitcoins from ransomware victims yet, because many victims use Tor proxies instead of installing the Tor browser, the potential impact is high for victims attempting to pay the ransom and decrypt their files. Ultimately, this type of activity undermines the somewhat dubious trust relationship that underpins the ransomware business. While this is not necessarily a bad thing, it does raise an interesting business problem for ransomware threat actors and practical issues for ransomware victims by further increasing the risk to victims who would resort to paying ransomware ransoms. This kind of scheme also reflects the broader trend of threat actors of all stripes targeting cryptocurrency theft. Continued volatility in cryptocurrency markets and increasing interest in the Tor network will likely drive further potential abuses of Tor proxies, creating additional risks for new users.
References
[1] https://www.pcrisk.com/removal-guides/11947-locker-ransomware
[2] https://blog.fortinet.com/2017/08/05/analysis-of-new-globeimposter-ransomware-variant
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
7cf39ebb4409b13a7c153abff6661cc4d28d8d7109543d6419438ac9f2f1be57 |
SHA256 |
LockeR ransomware |
|
lockerrwhuaf2jjx[.]onion |
Domain |
LockeR ransomware C&C |
|
ae0d28e8d57329866624ec6cf63b9609fe9e685200029d3aa207eda67747fcd7 |
SHA256 |
GlobeImposter ransomware |
|
bcwfga5ssxh3jrlp.onion |
Domain |
GlobeImposter ransomware C&C |
|
8f66bb494b3fc3063b18a18a51c7b85da90dc1bb429ded21e7dbb02b404d3831 |
SHA256 |
Sigma ransomware |
|
yowl2ugopitfzzwb[.]onion |
Domain |
Sigma ransomware C&C |
|
onion[.]top|46.246.120.179 |
Domain|IP |
onion[.]top Tor Gateway |











