Key Findings:
- Proofpoint first identified and named DanaBot in May 2018.
- Initially developed as a banking trojan, DanaBot was also used as an information stealer and loader for follow-on malware.
- Multiple prominent cybercrime actors favored DanaBot from 2018 through 2020, and the malware saw a resurgence in email since mid-2024.
- Some activity in 2019 and 2020 demonstrated an espionage focus for a small number of DanaBot campaigns.
- U.S. and international law enforcement disrupted DanaBot infrastructure as part of ongoing Operation Endgame efforts.
Overview
DanaBot is a cybercrime malware-as-a-service that Proofpoint researchers first identified and named in May 2018. At the time, banking trojans were the most popular email-based cybercriminal malware threat, and DanaBot became one of the favored payloads by TA547 before being adopted by other notable cybercrime threat actors.
The malware went through multiple updates and included different modules for loader and malware functionality as well as multiple anti-analysis features. Proofpoint initially identified some similarities in its technical implementation and characteristics to earlier malware, in particular Reveton and CryptXXX ransomware.
Although Proofpoint researchers named the malware DanaBot after a colleague suggested we name it after her, the threat actor began selling DanaBot under this name.
From 2018 through 2020, DanaBot was delivered by prominent cybercriminal groups including TA547, TA571, and TA564 before all but disappearing from the email threat landscape in mid-2020. In the last year, it has reappeared in email threat data much more frequently. DanaBot’s decline in email threat activity aligned with the overall decrease in banking trojans and the rise of malware focused on botnet, loader, and information stealer capabilities like IcedID and Qbot as precursors to ransomware delivery.
Campaign Details
As a malware-as-a-service, DanaBot sold access to a small group of ecrime affiliates. Proofpoint tracked at least a dozen different affiliate IDs associated with DanaBot campaigns, and typically each threat actor used unique affiliate IDs. For example, TA547 regularly distributed DanaBot Affid 5 and Affid 6, and TA564 distributed Affid 11.
While it was not as prevalent in Proofpoint’s email threat data from 2020 through 2024, threat actors continued to distribute DanaBot via other initial access methods including SEO poisoning and malvertising campaigns that in some cases led to ransomware.
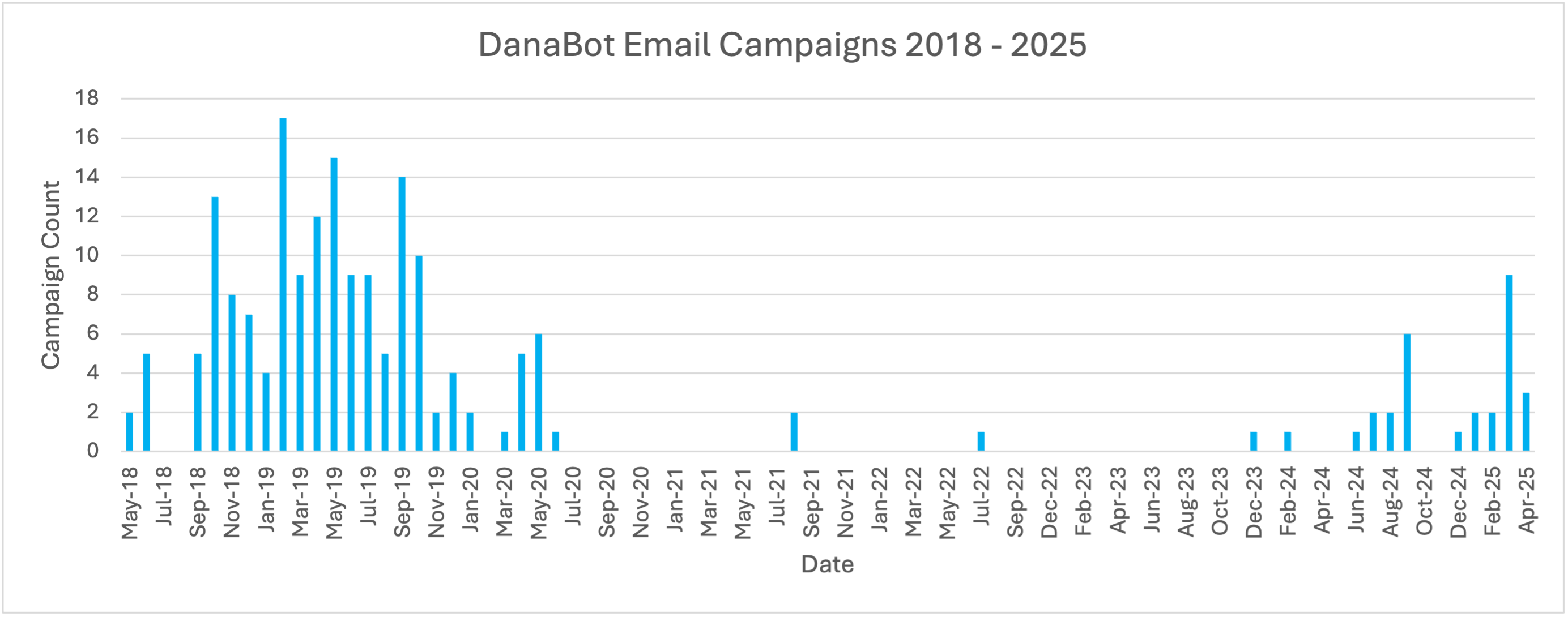
Number of DanaBot campaigns observed in Proofpoint email threat data, May 2018 to April 2025.
Based on our visibility, DanaBot was nearly entirely absent from the email threat landscape from July 2020 through December 2023 with just a handful of campaigns during this time that were not attributed to tracked threat actors. However, Proofpoint observed prominent ecrime actors TA578 and TA544 deliver DanaBot in one campaign each in December 2023 and February 2024, respectively. Our researchers have not observed either of these actors use DanaBot previously or since. Notably, in the TA578 campaign, DanaBot dropped Latrodectus. While Proofpoint did not observe these DanaBot campaigns lead to ransomware, both TA544 and TA578 initial access activities have been previously associated with ransomware infections.
Beginning in mid-2024, Proofpoint observed a reemergence of DanaBot email campaigns, with the majority of campaigns attributed to two main activity clusters. These campaigns can lead to data or financial theft or enable follow-on activities such as ransomware.
Recent Campaigns
Example 1: Group targeting logistics
Proofpoint is tracking a sophisticated criminal threat actor targeting transportation and logistics firms that often leverages compromised accounts and thread hijacking to distribute malware including DanaBot. These campaigns are low volume (less than 100 messages per campaign) and highly targeted to trucking, transport, shipping, and logistics firms. Other payloads used by this actor include Lumma Stealer, StealC, and NetSupport.
For example, on 24 March 2025, Proofpoint researchers observed the actor using brand impersonation and a combination of actor-controlled or compromised senders to conduct a campaign leading to DanaBot.
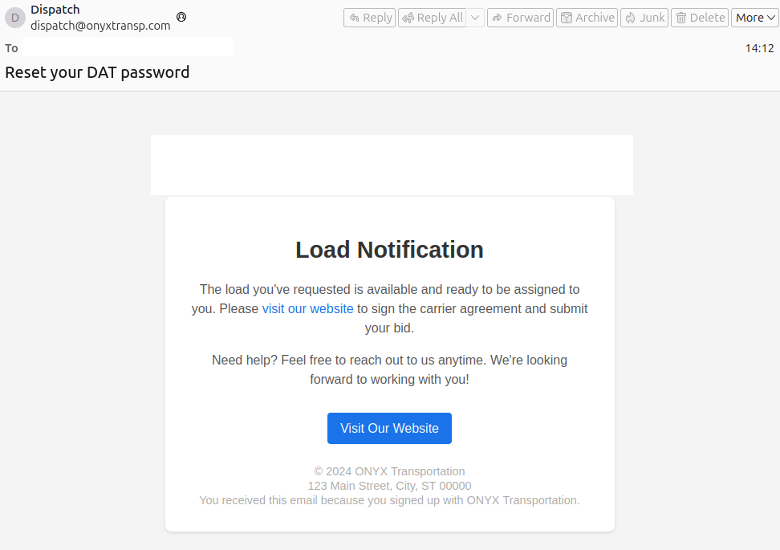
Phishing email impersonating a transport company.
In this campaign, messages contained URLs which resolved to a website with a search:query link that pointed to a Microsoft Shortcut (LNK) file. If executed, the LNK file used PowerShell to download and run an executable file that used Peaklight (aka Emmenthal Loader) to display a decoy PDF and download and run an executable file that installed DanaBot.
Example 2: Reservation themed campaigns
Another highly active criminal threat activity cluster distributing DanaBot regularly impersonates travel booking firms and leverages the reCAPTCHA ClickFix technique to deliver malware. These campaigns are higher volume with up to 6,000 messages per campaign, and target organizations in hotel, travel, and hospitality industries. Other payloads delivered by this activity set include XWorm, Amadey, DOILoader, zgRAT, NetSupport, and Lumma Stealer.
For example, in early March, Proofpoint observed a campaign using Gmail senders with subjects related to hotel reservations to distribute DanaBot.
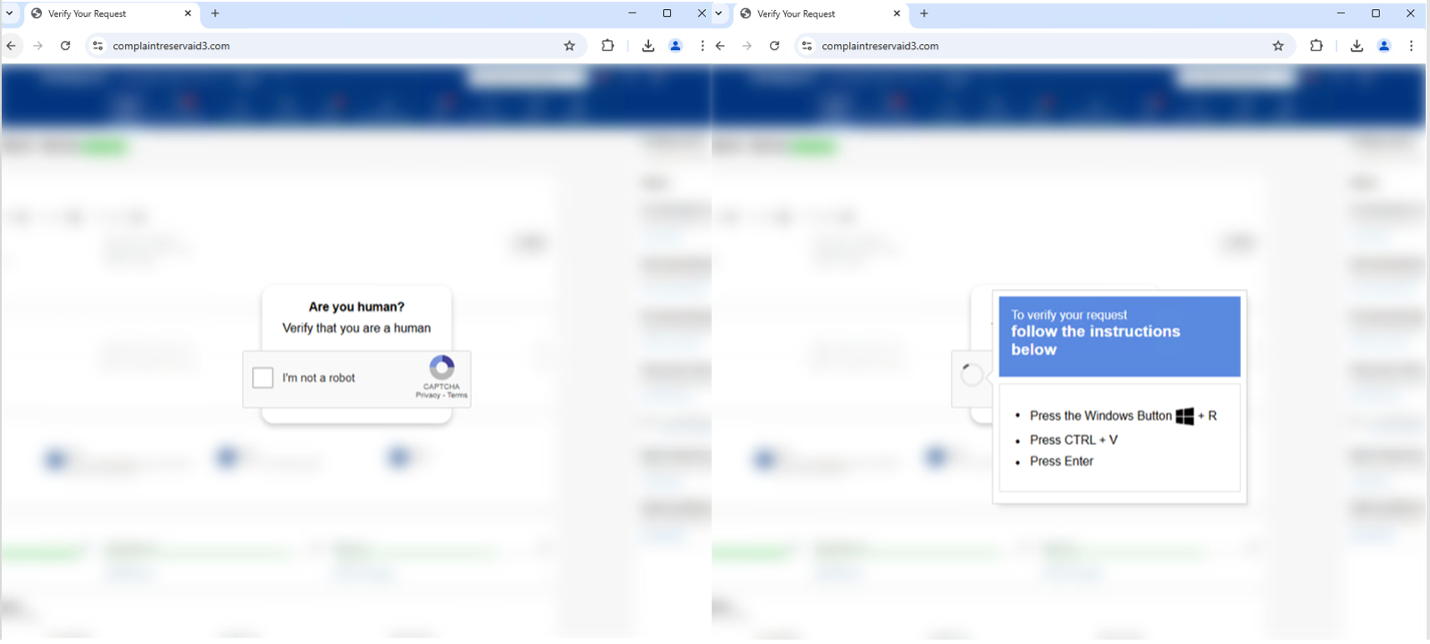
ClickFix instructions if a target clicked the URL, impersonating Booking.
Messages contained URLs, that if clicked, presented a web page with a Booking themed lure using the ClickFix technique. If the user copied and pasted the PowerShell script as instructed, it executed a second PowerShell script ultimately leading to DanaBot.
Overlap with Espionage
In October 2019 and January 2020, Proofpoint researchers observed a small number of campaigns distributing DanaBot that deviated from typical cybercriminal campaigns. The messages impersonated the Organization for Security and Co-operation in Europe (OSCE) and a Kazakhstan government entity to deliver DanaBot.
These campaigns were very low volume and targeted entities in government, defense, and non-governmental organizations. The lures were related to the security situation in Ukraine, security training efforts, and government exports from Central Asia. One campaign included Russian language lures. In a campaign impersonating OSCE, threat actors included language directly copied from a public report on the organization’s website.
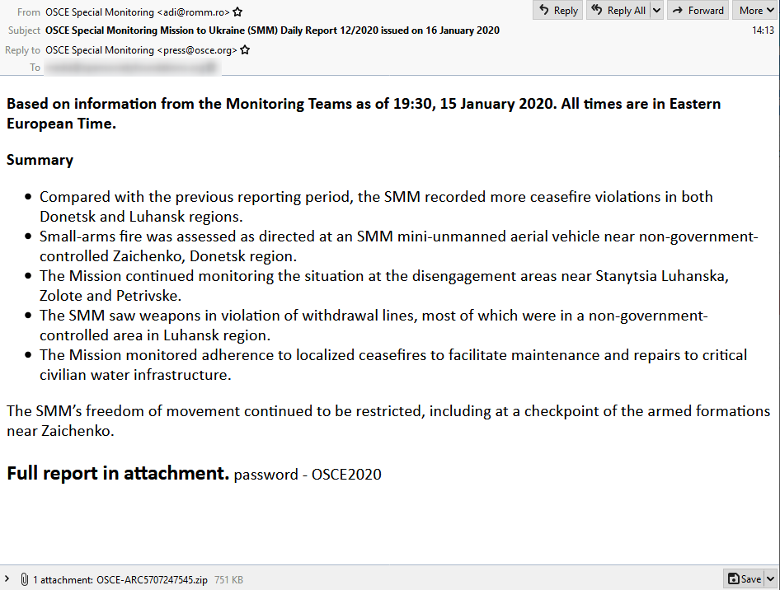
Email lure impersonating OSCE, observed by Proofpoint.
In all campaigns, messages included password-protected, zipped VBS attachments (or URLs leading to the same) that ultimately installed DanaBot with Affid 25.
These campaigns were the only time Proofpoint researchers observed Affid 25, and the only campaigns that deviated from typical criminal campaigns. Characteristics that indicated an espionage objective included: highly targeted activity impacting a small number of individuals in organizations related to defense and government; lure content aligning with typical espionage themes, including mention of security monitoring in Ukraine; and capabilities of the DanaBot variant used that focused on information gathering. Proofpoint assesses with high confidence these activities were likely conducted to align with Russian government espionage objectives.
The activity is notable as it shows how the lines between cybercrime and espionage activities can often be blurry, and malware typically considered cybercrime can be used for information gathering or spying purposes. Historically, there are multiple examples of cybercriminals and ecrime malware operating on behalf of espionage objectives for example, Evil Corp and other prominent longtime cybercriminal threat actors.
Operation Endgame Disruption
On 22 May 2025, international law enforcement and the U.S. DOJ, DCIS, and FBI announced the disruption of DanaBot and related infrastructure, as well as named multiple individuals allegedly associated with the malware creation and distribution. The disruption was part of ongoing efforts known as Operation Endgame.
Operation Endgame is a widespread effort conducted by global law enforcement and private sector partners, including Proofpoint, to disrupt malware and botnet infrastructure and identify the alleged individuals associated with the activity. In May 2024, the first Operation Endgame disruption effort targeted multiple malware families including IcedID, Bumblebee, SystemBC, Pikabot, SmokeLoader, and more, and Europol called it the “largest ever operation against botnets, which play a major role in the deployment of ransomware.”
The Operation Endgame disruptions in May 2024 had a significant impact on the overall email threat landscape, specifically disrupting activity attributed to known initial access brokers (IABs) conducting email-based campaigns. For example, in March 2023, 17% of email campaigns in Proofpoint data were attributed to known IAB or related threat actors and activities targeted by Operation Endgame, while that number had dropped to just 1% by February 2025.
The threat actors currently using DanaBot in email campaigns also deliver other malware, so it is likely their activity will continue, and they may adopt new payloads to replace DanaBot. However, the disruption and naming and shaming activities will impose cost to other threat actors more reliant on DanaBot as their main payload and will also likely sow distrust among the cybercriminal ecosystem as law enforcement continues to disrupt and malign creators, sellers, and distributors of malware, especially those that support the ransomware ecosystem.
Conclusion
As law enforcement disruptions continue to impact threat actors’ behavior, it’s important to be aware of emerging trends and behaviors from prominent cybercriminal threat actors, such as the use of remote monitoring and management software (RMMs), increase in use of information stealers, and new social engineering techniques that target people not technology. It’s also important to understand how espionage focused threat actors have increasingly adopted cybercriminal techniques – and sometimes leverage the actors or malware themselves – for government-backed campaigns. By understanding the landscape, organizations can implement defenses against emerging trends and anticipate what decisions threat actors will make to stay ahead of them.
Proofpoint’s mission is to provide the best human-centric protection for our customers against advanced threats. Whenever it is possible and appropriate to do so, and as is the case with Operation Endgame, Proofpoint uses its team’s knowledge and skills to help protect a wider audience against widespread malware threats. Proofpoint was proud to assist in the law enforcement investigations into DanaBot activity.
Through its unique vantage point, Proofpoint is able to identify the largest and most impactful malware distribution campaigns, providing the authorities with much-needed insight into the biggest threats to society, affecting the greatest number of people around the world.











