New research points to OneDrive and SharePoint ransomware risk. And more insights from this year's Human Factor report.
This week on The Threat Hub: Moving to the cloud has made document management simpler in many ways. Changes are saved automatically, version history stores a timeline of multiple copies, and documents can be accessed from mobile devices for editing and sharing on the go. And to cap it all, cloud drives are hosted on the infrastructure of some of the world’s biggest tech companies, making them safer and more resilient against attack. But new research from our cloud security division reveals a potential ransomware risk existing in plain sight on Microsoft SharePoint and OneDrive accounts.
Using legitimate functionality, an attacker with access to a compromised drive can manually adjust the number of saved versions of a document down to one so it stores only the most recent copy. Then all they need to do is overwrite that file twice with encrypted versions, and the account owner will be unable to recover an unencrypted copy from the drive’s version history. This method even permits the attacker to download the original files for use in double extortion before encrypting the cloud-stored versions. Check out the blog for a full description of the likely attack chain, and a list of potential mitigations suggested by our researchers.
And on this week’s Five-Minute Forecast, “Icefall” vulnerabilities put thousands of critical systems at risk, BlackCat ransomware ups its shame game, and Sherrod DeGrippo shares her perspective on key insights from this year’s Human Factor report.
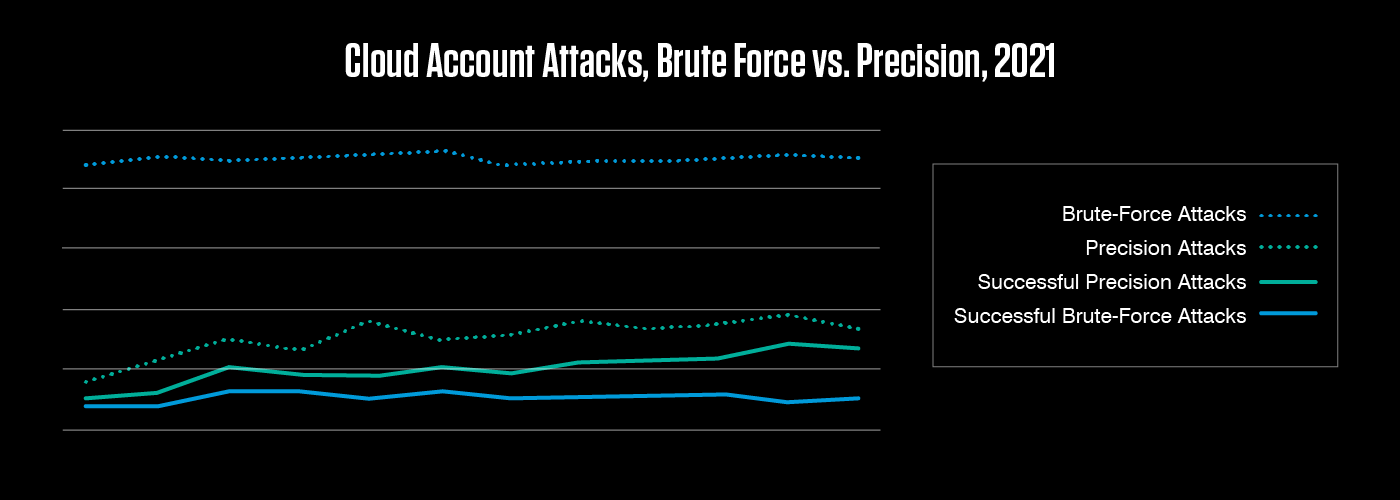
New data from the latest Human Factor report shows that brute-force cloud account attacks are now extremely common, and that the number of successful precision attacks is rising.
Get the reportEquip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyberattackers target people. They exploit people. Ultimately, they are people. That’s why the Human Factor report focuses on how technology and psychology combine to make people so susceptible to modern cyber threats. In this first volume, we take a closer look at attacks that rely on social engineering, including business email compromise (BEC) threats, email fraud and phishing.
In 2021 the spotlight of global attention fell on cyber criminals like never before. In our first semiannual threat update, we explore new techniques and old tricks in a rundown of the year's biggest themes and schemes.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.