Less than 20 years ago, only 5% of Americans used social media. Today, the figure stands at 72% as platforms like Facebook, Twitter, Instagram, TikTok and countless others weave themselves into the fabric of everyday life.
In the process, social media has also become a hotbed for crime. According to the U.S. Federal Trade Commission (FTC), more than 25% of reported fraud in 2021 originated on social media. And the victims are not necessarily who you would expect. It’s not just older people who are falling victim to social media fraud; all demographic groups are affected. In fact, the FTC reports that people between the ages of 18 and 39 were more than twice as likely as those over 40 to fall victim to social media scams in 2021.
About this series
Today’s cyber threats rely on human interaction, not just technical exploits. In fact, 82% of data breached in Verizon’s “Data Breach Investigations Report” involved the human element. As the report puts it, this reality “puts the person square in the center of the security estate.” Attackers use social engineering to trick people into clicking unsafe URLs, opening malicious attachments, entering their credentials, sending sensitive data, transferring funds and more.
This is the fourth of our six-part blog series covering several topics you should address in your security awareness training for October's Cybersecurity Awareness Month. This series will cover:
- Social engineering
- Phishing
- Business email compromise (BEC)
- Social media
- Ransomware
- Insider risk
How attackers exploit people on social media
Attackers use social media to achieve several goals, including:
- Gaining access to a users’ credentials
- Installing malware on users’ devices
- Stealing money from users
Why social media?
Attackers love social media because most people have at least one social media account. Because social media is informal and part of peoples’ personal lives, many users lower their defenses when using these platforms. And they often use social media at times when they are tired or distracted, such as in the evenings after work or waiting in line. All of this adds up to make social media an easy target for attackers.
Types of social media attacks
Users of social media face are many types of threats. Attackers typically use several activities to lure users into providing personal information, credentials or money.
Impersonation
Attackers pretend to be someone a user knows or a representative from an institution they trust, such as the Internal Revenue Service or the Social Security Administration.
For example, your employee may receive a message that appears to come from a friend. The friend claims that they are stuck overseas after being robbed. And they need your employee to send money urgently to help them get home.
Or your employee might receive a message from the Social Security Administration saying that they have been trying to contact them and need them to take urgent action (such as clicking on a link to log into your account or confirm their address).
Healthcare fraud
These scams use healthcare topics that are top of mind, such as COVID-19 or monkeypox. Users are enticed to click on a link or provide personal information in exchange for:
- Testing kits, which fail to materialize or are fake
- Fake COVID-19 vaccination cards
- Vaccines, treatments and remedies, which are often fake
Attackers will also offer money or gifts in exchange for completing “surveys” about vaccination or treatment. These “surveys” are vehicles for stealing personal data, medical information or financial details.
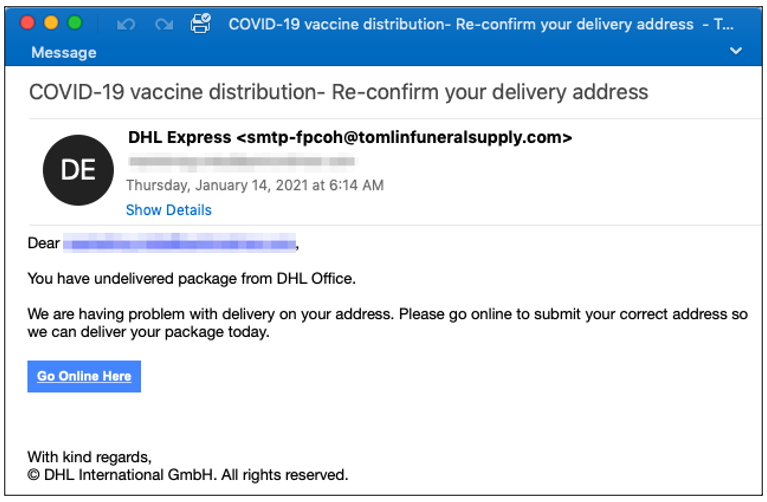
Figure 1: A screenshot of an email purporting to inform the recipient about an undelivered DHL vaccine package.
Clickbait
Clickbait scams lure users to click on malicious links with promises of shocking or embarrassing content. Users may receive a private message (often appearing to come from a trusted friend) that suggests the sender has found a lewd or otherwise compromising photo or video of the recipient.
When the user clicks on the link to view the media, they are prompted to update software required to view it and end up installing malware. Because people will want to quickly get the photo or content removed and experience feelings of embarrassment and potential shame, they are less likely to stop and check if the link that is being sent is safe. This is just one of the many ways that attackers leverage emotions.
Phishing
Social media phishing happens in two main ways.
In the first, attackers send emails that appear to come from a social media platform. The email explains that the user’s account password has been compromised. The user is instructed to click on a link to maintain access to their account. This link leads to a fake login page that harvests the user’s credentials. This works because attackers have targeted the user's emotions and a sense of urgency, as the user now feels they have to act fast to restore their social media account to safety.
In the second type of social media phishing attack, users receive friend requests from people that they appear to know. These accounts, which are either compromised or faked, post content with malicious URLs that lead to a fake login page. From a social engineering standpoint, the attackers try to exploit people's basic desire to connect and build social, interpersonal relationships with others. This makes it likely that users will be motivated to click on friend requests quickly and without verifying that person's identity.
Romance scams
Romance scams are a form of impersonation scams. In a romance scam, attackers adopt a fake identity to foster a romantic relationship with a user, sometimes over a long period of time. Once trust has been established, they usually manipulate the user into sending money.
In September 2021, a former U.S. Army reservist was sentenced to 46 months in prison for his role in a scheme to swindle more than $1.8 of dollars from nearly 70 victims across the country. The scheme created fake identities to dupe older men and women into believing they were in romantic relationship, then exploiting their emotions to get money from them.
And who hasn’t heard of the notorious “Tinder Swindler” (a.k.a. Shimon Hayut, a.k.a. Simon Leviev)? Posing as the playboy son of a diamond tycoon, Hayut lavished women with gifts, attention and whirlwind vacations—before asking them for money to fend off mysterious “enemies.”
Sweepstakes and lottery scams
Sweepstakes and lottery scams use promises of prize winnings as a lure for users to provide personal or financial information. Attackers know that users will always be interested in the promise of winning money, so they hope that they will appeal to a person's desire to feel excitement and joy to click quickly.
Quizzes and polls
Quizzes and polls that appear in social media feeds may seem like a fun and harmless activity. But attackers often use quiz scams to harvest personal information from users, including answers to common security questions.
Remote work and money-making schemes
These scams are a form of employment fraud. Attackers pretend to be recruiters and lure users with advertisements for high-paying, easy work that can be done from home. These remote work job scams are merely a front for stealing personal information and money from the users who respond to them.
How these scams impact your organization
Although most of your employees are unlikely to use social media as part of their regular job duties, social media attacks have the potential to harm your company. If an employee’s device or accounts become compromised through one of these attacks, it can give attackers a foothold to launch an attack within your company. Given that in today's remote work environment people use their personal devices for work and personal life, it means that any attack can compromise sensitive information and data from work that can cripple organizations.
Tips for your end users
You can help your employees understand how to safely engage with social media by sharing the following tips:
- Always treat requests for money and credentials with extreme suspicion, even if they appear to come from someone you know. If you receive a request for your money or credentials, always contact the person through another channel to verify.
- Beware of promotions, job advertisements and pop-up messages making promises that seem too good to be true.
- Don’t enter your username or password into websites unless you have navigated to the site directly and verified the URL in your browser.
- Delete any requests for sensitive data and report them to your security team if you receive them on company accounts.
- Only contact social media support and contacts by navigating to the social media website or app directly.
- Watch out for messages that ask for money urgently, even if they come from someone you know. Always take your time to check in outside of social media with the person making the request.
- If you think your account has been compromised, immediately log in and reset your username or password. If you have trouble, report it to the social media site.
- Don’t open social media websites in the same browser window as your banking website or other sensitive sites. Attackers can sometimes capture important information this way.
Up next: more end user security awareness topics
The next blog in this security awareness training topic series will help educate your employees on ransomware. We will cover how users can protect their organization against ransomware as part of a people-centric approach.
Visit the Proofpoint Cybersecurity Awareness Hub for more security awareness resources. Proofpoint Security Awareness can also help you build a security culture that drives positive behavior change.











